

Written By Hugh Brooks , Director of Security Operations at CertiK
Scams are nothing new. Each of the methods detailed below are merely variations on themes that have been around for centuries, if not longer. Yet the intersection of social media and cryptocurrency has formed a potent breeding ground for scams. Social media's accessibility and broad reach make it a fertile arena for fraudsters, while the decentralized and often opaque nature of cryptocurrency offers a convenient cloak for deception.
Together, they create a “combustible combination”, in the words of the Federal Trade Commission (FTC), which said in a report that of the more than $1 billion lost to crypto scams in the 18 months to June 2022 almost half “started with an ad, post, or message on a social media platform.”
One in four people who reported losing money to fraud of any type identified social media as the starting point of their troubles. The growth of crypto scams is not merely a reflection of the rising popularity of digital currencies but also an indicator of the evolving sophistication of scammers.
The objective of this article is not to alarm but to enlighten. This comprehensive guide aims to equip you with the tools and knowledge needed to recognize and avoid common crypto social media scams. By delving into the common mechanisms of crypto social media scams, you’ll come away equipped with the tools and knowledge you need to spot and evade these traps. Read on to better understand the landscape of crypto social media scams and navigate it safely. We’ll do it with the help of some historical parallels that will shed light on the underlying mechanisms of these scams and make it easier to identify new instances in the future.
Common Crypto Social Media Scams
Pump and Dump Schemes
“Pump and dump” schemes involve assets being artificially inflated in value only to be sold off for profit. The creation and promotion of small-cap cryptocurrencies, sometimes by celebrity influencers, provides fertile ground for manipulation.
 A typical pump and dump chart, in this case EthereumMax, which was promoted by Kim Kardashian. Source: CoinGecko
A typical pump and dump chart, in this case EthereumMax, which was promoted by Kim Kardashian. Source: CoinGecko
Legal authorities have recognized the threat, with the Securities and Exchange Commission (SEC) cracking down on influencers who promote risky and unvetted tokens. In a series of charges in 2022 and 2023, celebrities and crypto entrepreneurs alike have faced legal scrutiny for their involvement in such practices.
Historical Parallel: This practice has been observed in various stock markets for centuries. Perhaps the most famous example is the South Sea Bubble in 1711. The South Sea Company inflated the value of its shares through false claims and speculation, only for it to collapse and lead to financial ruin for many investors.
Read more: Web3 Celebrity Endorsements
Fake Verification Ticks
The blue verification tick on social media platforms such as Twitter, Facebook, and Instagram has come to symbolize trustworthiness and authenticity. However, this symbol of validation has been weaponized by scammers who manipulate these trust signals to their advantage. Exploiting the very emblem meant to instill confidence, scammers either acquire verified accounts or craftily incorporate a blue check into profile pictures and wallpapers to appear authentic.

Even with platforms like Twitter taking measures to shut down fake accounts, scammers still find ways to create convincing imitations. Recent instances include the surge of fake accounts following Elon Musk's introduction of paid verification. This misuse of verification badges isn't merely a deceptive aesthetic; it enables scammers to promote fraudulent projects, post phishing links, and sway investment decisions in the crypto space. This trend emphasizes the need for careful scrutiny of social media handles, even those with seemingly "verified" status.
Historical Parallel: During medieval times, forgery of royal and noble seals was a common way to fabricate the authenticity of documents. The Great Seal of the United Kingdom, for instance, has been counterfeited in attempts to forge royal decrees or land grants.
Fake Applications
Fake apps pose as legitimate applications for cryptocurrency trading or as secure wallets, but these fraudulent apps serve as trojan horses for swindlers. Once downloaded, they may either stealthily install malware on the user's device or directly steal funds deposited into the app. A sense of authenticity is often fabricated by distributing these apps through official channels like the Apple App Store and Google Play Store.
The FBI's latest fraud report underscores the gravity of this threat. In 2021, Americans lost approximately $42.7 million to criminals through deceptive applications. Fake crypto apps not only siphon money but also gather personal information that can lead to broader breaches of financial security. Awareness of this threat and the careful evaluation of an app’s legitimacy is crucial for anyone engaging in mobile cryptocurrency transactions, storage, or trading.
Historical Parallel: The "snake oil" salesmen would travel across America selling fraudulent medicines that claimed to cure a multitude of ailments. The packaging, promotion, and presentation were all carefully designed to imitate genuine products. In reality, they contained no beneficial ingredients and often were harmful.
Read more: BombFlower Backdoor: Uncovering an Evasive Fake Wallet Campaign
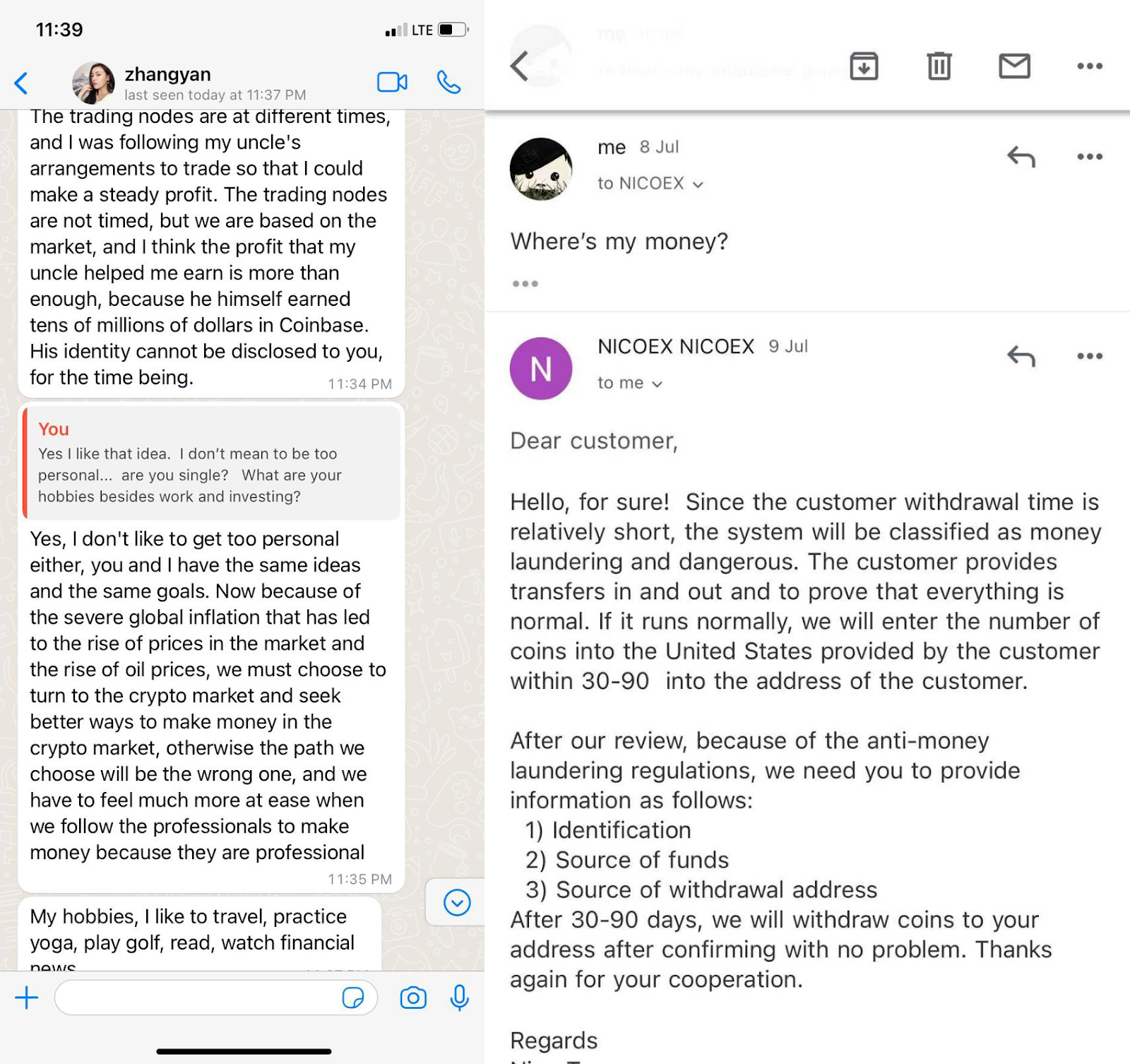
Romance Scams
Romance scams, euphemistically termed “pig butchering,” are another form of scam that begins on social media and often ends in the irreversible transfer of crypto assets. The term "pig butchering" might seem oddly out of place in a financial context, yet it encapsulates an insidious form of crypto fraud that has gained traction in recent years. In these schemes, swindlers build trust with their victims (the pigs) over time, using social media, dating apps, or texting. Posing as successful traders, they promise to multiply life savings through crypto or forex trading. As the trust grows, so does the victims' investment, until the scammers vanish with the money – butchering them.
 Source: Global Anti-Scam Organization
Source: Global Anti-Scam Organization
According to the FBI, pig butchering scams were responsible for over $429 million in losses in 2021. The demographic profile of victims reveals some surprising characteristics: 67% are women aged 25-40, with an overrepresentation of graduate degree holders at 32%. Losses can be catastrophic, with 75% losing at least half their net worth, and one-third being driven into debt.
The deception includes the creation of fake websites and apps that convincingly display the rapid growth of the victim's investments. When they attempt to cash out, hurdles are placed in the form of taxes or fees, further bleeding the unsuspecting targets.
Avoiding these scams requires vigilance and skepticism. The FBI advises thorough due diligence on investment opportunities, careful evaluation of domain names, cautious downloading of apps or software, and a healthy dose of skepticism towards promises of guaranteed returns.
The rise of pig butchering scams underlines the evolving complexity of crypto-related fraud. It's not merely the technology that requires understanding but human psychology and social engineering. These scams exploit trust, vulnerability, and greed, reminding us that the oldest tricks in the book can be dressed in the newest of technological outfits.
Historical Parallel: Casanova, the famous 18th-century figure, was known not only as a lover but also a scam artist who utilized romance and charm to deceive and defraud. His memoirs document numerous financial schemes where he leveraged his personal connections.
Read more: The $400M Crypto “Pig Butchering” Industry: How to Avoid the Slaughter
How to Recognize Crypto Social Media Scams
Recognizing Fake Influencer Endorsements
The prevalence of social media influencers has given rise to an environment ripe for exploitation through fake endorsements. In the crypto world, scammers may use doctored images or counterfeit profiles to mimic influencer support for various projects or products. Verifying influencer authenticity becomes vital, and this can be achieved by cross-referencing the influencer's other social media platforms, checking for verification ticks, and being wary of suspicious activity like rapid follower growth. Common red flags may include inconsistent messaging, unfamiliar endorsement practices, or endorsements for products that don't align with the influencer's known values or interests. Sometimes, real influencers will still promote low-quality or outright scammy projects, so it’s important to always be careful when following these sorts of opaque endorsements.
Spotting Fake Apps
Identifying and avoiding fake apps demands careful scrutiny. Always download apps from reputable sources like official app stores and pay attention to details such as the developer's name, company information, and application description. If anything appears suspicious, such as misspellings or mimicking well-known brands, it's a signal to proceed with caution. Checking the developer’s website for authenticity and reading user reviews can further safeguard against accidentally downloading a fraudulent app that could compromise personal information or assets.
How to Stay Safe
1. Utilize a Hardware Wallet
Hardware wallets are physical devices that store private keys offline. They offer robust protection against online hacking attempts. By keeping the keys isolated from the internet, these devices create a barrier that is virtually impervious to theft. In most cases, an attacker would require physical access to the device, along with the passcode securing it, in order to steal the assets.
However, hardware wallets are not impervious to phishing attacks. If you grant permissions to a malicious contract, you may still find your assets gone. But a hardware wallet requires physical confirmation of the transaction, so it gives some additional time to consider it before executing. Try to tell yourself why you’re submitting the transaction you’re about to submit. If you’re not sure, take a second.
2. Multi-Signature Wallets (with Timelock)
Multi-signature wallets require multiple private keys to authorize a transaction. The integration of a timelock adds an additional layer of security. Timelocks can enforce a waiting period before a transaction is finalized, providing time to detect and counteract unauthorized actions. By requiring multiple approvals and incorporating time-based restrictions, the security level protecting one's assets is strengthened, reducing the risk of unauthorized access.
3. Smart Contract Security Audits
In a space where smart contracts play a pivotal role in transactions, engaging in security audits becomes paramount. These audits, often conducted by specialized third-party experts, scrutinize smart contract codes to identify vulnerabilities and ensure that they function as intended. Through a rigorous examination of potential weak points, these audits contribute to the secure and efficient operation of smart contracts within the decentralized landscape of crypto. If a contract is designed to scam users, an audit will point that out. However, it’s important to note that an audit cannot solve the vulnerabilities in a contract, it’s up to the developers to do that. An audit points out the red flags wherever they may exist.
General Best Practices
Getting involved with cryptocurrency demands critical thinking and a healthy degree of skepticism. Regularly updating and using legitimate security software, adhering to secure password practices, and utilizing only trusted exchanges and platforms are foundational to maintaining the integrity of one's investments. In a space defined by innovation and transformation, the marriage of traditional wisdom with avant-garde technology paves the way for safe and confident participation in the crypto ecosystem.
Conclusion
The confluence of cryptocurrency's rise in prominence and social media's ubiquitous reach has led to a proliferation of crypto social media scams. These scams are not isolated to crypto, they’re merely the application of old techniques to a new industry. From pump-and-dump schemes to the pernicious "pig butchering" frauds, the threat is real, multifaceted, and growing.
However, this should not overshadow the transformative potential of the crypto world or paralyze us with fear. Instead, it should serve as a call for education, vigilance, and the application of best practices. Utilizing tools such as hardware and multi-signature wallets can help safeguard assets, and add a vital extra layer of consideration before sending any transaction. Coupled with a mindset grounded in critical thinking, secure habits, and continuous learning, these practices form a robust defense against scams. The historical parallels in this article should serve as beacons, illuminating that what might seem novel or peculiar in the world of crypto scams can often be understood in the context of human history and behavior. By understanding the past, we can safely embrace the future.
Frequently Asked Questions
What is the scale of losses from crypto social media scams?
According to the Federal Trade Commission (FTC), over $1 billion was lost to crypto scams in the 18 months leading up to June 2022, with almost half of those starting on social media platforms. This represents one out of every four dollars reported lost to any form of fraud.
What are some common types of crypto social media scams?
There are several common types of scam, including "pump and dump" schemes that involve artificially inflating the value of assets; fake verification ticks on platforms like Twitter, Facebook, and Instagram; fake applications that pose as legitimate cryptocurrency trading platforms; and romance scams or "pig butchering" where trust is built over time to defraud victims.
How are verification ticks misused on social media for scams?
Scammers weaponize blue verification ticks on social media by either acquiring verified accounts or craftily incorporating a blue check into profile pictures and wallpapers to appear authentic. This enables them to promote fraudulent projects, post phishing links, and sway investment decisions in the crypto space. Even with measures to shut down fake accounts, scammers are still finding ways to create convincing imitations.
What is a "pig butchering" scam?
"Pig butchering" scams involve swindlers building trust with their victims over time through social media or other platforms, posing as successful traders. They then persuade the victims to invest in crypto or forex trading, eventually disappearing with the money. The FBI reported that in 2021, these scams were responsible for over $429 million in losses. Many victims lose large portions of their net worth, and some are driven into debt.
What tools and practices can be used to stay safe from crypto scams?
Some of the key practices to stay safe include utilizing hardware wallets that store private keys offline; implementing multi-signature wallets with timelocks, which require multiple private keys and time-based restrictions; engaging in smart contract security audits; and adhering to secure password practices, regularly updating security software, and using only trusted exchanges and platforms.
This article was originally published on BeInCrypto.